Research Symposium
25th annual Undergraduate Research Symposium, April 1, 2025
Kien Le Poster Session 3: 1:45 pm - 2:45 pm/ Poster #169

BIO
Welcome to my profile! My name is Kien, a second-year student majoring in Computer Science. Originally from Vietnam, I have a strong interest in machine learning, artificial intelligence, and cybersecurity. My research focuses on adversarial machine learning, particularly the vulnerabilities of Graph Neural Networks (GNNs) in security-sensitive applications. Through the UROP program, I have been working on model extraction attacks against GNNs to better understand how attackers can replicate AI models under resource constraints. Beyond research, I am passionate about exploring the intersection of AI security and efficient machine learning techniques. My long-term career goal is to pursue research in academia, contributing to advancements in AI and the development of more robust and trustworthy machine learning systems.
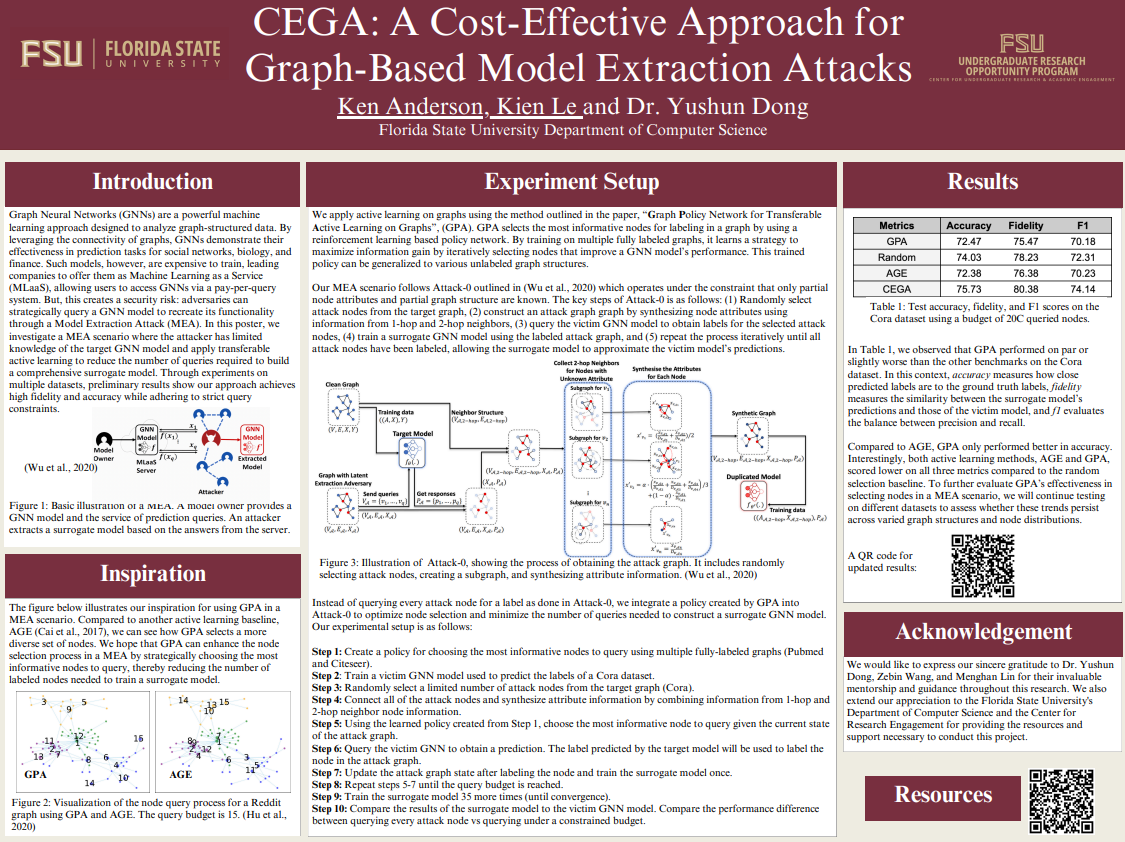
CEGA: A Cost-Effective Approach for Graph-Based Model Extraction Attacks
Authors: Kien Le, Yushun DongStudent Major: Computer Science
Mentor: Yushun Dong
Mentor's Department: Computer Science Mentor's College: Arts and Sciences Co-Presenters: Ken Anderson
Abstract
Graph Neural Networks (GNNs) are a powerful machine learning approach designed to analyze graph-structured data. By leveraging the connectivity of graphs, GNNs demonstrate their effectiveness in prediction tasks for social networks, biology, and finance. Such models, however, are expensive to train, leading companies to offer them as Machine Learning as a Service (MLaaS), allowing users to access GNNs via a pay-per-query system. But, this creates a security risk: adversaries can strategically query a GNN model to recreate its functionality through a Model Extraction Attack (MEA). In this poster, we investigate a MEA scenario where the attacker has limited knowledge of the target GNN model and apply transferable active learning to reduce the number of queries required to build a comprehensive surrogate model. Through experiments on multiple datasets, our approach achieves high fidelity and accuracy while maintaining strict query constraints.
Keywords: AI, Machine Learning, Graph Neural Networks, Math, Security, Neural Network